#cybersecurity
#Phishing
@Microsoft
All posts by admin
Vulnerability Assessment Survey
The security operations maturity self- assessment helps you evaluate how prepared your security operations team is to detect, respond and recover from cyber-attacks. Use this tool to determine the stage in security maturity model you’ve reached and get recommendations for processes and tooling that can increase preparedness.
Announcing a New Dynamics 365 Supply Chain Management Consultant Functional Consultant Expert Certification
Looking to update your supply chain management skills? Microsoft announced a new Microsoft Certified: Dynamics 365 Supply Chain Management Functional Consultant Expert certification for consultants, IT professionals and developers. Read the blog for details on requirements and how to stay up to date.
The Case for Cloud Adoption in Financial Services Grows Stronger
Cloud infrastructure and applications have become significantly more secure and the advantages of cloud computing have grown.
As financial services expert Yvonne Dunn notes, “The reasons for financial institutions to move systems and data to the cloud have never been more compelling – and the barriers to doing so are diminishing.” In this article, Dunn explains the key benefits driving financial services companies to adopt the cloud. Read the blog here.
Cloud Architecture Assessment
Once full migration to the cloud has been embraced, it is essential to get a complete picture of your entire cloud architecture to ensure you’re getting the most out of your investments while keeping data and your business secure. Book a free Cloud Architecture Assessment from the experts at Mowry International.
Six Trends That Are Shaping Supply Chain Transformation for Manufacturers
Supply chains have achieved major importance in manufacturing. Like other manufacturers, you depend on implementing the right supply chain strategies and technologies to stay competitive. In this report, you’ll learn about six emerging trends that are shaping how supply chain leaders succeed. With an understanding of these trends and their impacts, you can identify opportunities to be more agile, efficient and competitive.
Read the report here.
View: Six Trends That Are Shaping Supply Chain Transformation for Manufacturers
Social Message with Infographic
From enabling hybrid work to creating collaborative experiences—here’s what’s new in Microsoft 365
With organizations settling into hybrid work, the new challenge for organizations is to balance employee demands for flexibility with business needs. Read the blog to gain insight on how the new capabilities in Microsoft 365 are tackling these challenges.
Introducing Azure Well-Architected Framework Assessments for Azure Stack Hub (Preview)
Read this blog for insight on how the Azure Well-Architected Framework can help you make more informed decisions regarding cloud workload design, technology and implementation.
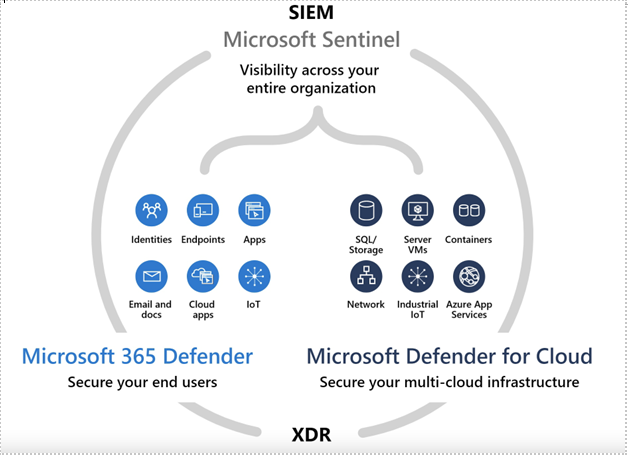
Keep application and user data secure
This infographic highlights the ease with which Azure Virtual Desktop keeps application and user data secure and removes the complexities of access management. View the infographic for an at-a-glance of how you can simplify access control across users and devices.