Your organization is being squeezed at all levels. Your IT department is no exception as it looks for creative ways to cut costs while dealing with growing application backlogs. One way forward? Low-code. In this blog, Microsoft GM Richard Riley looks at research showing how low-code empowers IT to rapidly build technical solutions and streamline data insights while lowering costs. Read the blog for insight and to learn where Microsoft Power Platform fits in.
All posts by admin
Co-op Group consolidates architecture stack with Azure Stack HCI
Discover how Co-Op, a retail industry pioneer, transformed infrastructure with Microsoft Azure. In this inspiring customer story, you’ll learn how Co-Op leveraged Azure’s scalable solutions to revolutionize operations, streamline processes and boost productivity. Gain valuable insights into the retailer’s journey from implementation to results. Discover the remarkable benefits of Azure. Get the story and envision the possibilities of Azure for your business.
Security is only as good as your threat intelligence
In today’s digital landscape, protecting your business from cyber threats is paramount. Our latest blog post delves into the crucial role of threat intelligence in safeguarding your organization. Gain valuable insights into the importance of proactive threat protection, how advanced tools enhance security and why you need a robust threat intelligence strategy. Reading this blog post is one step towards staying ahead of cyberthreats. Read the blog and take the lead.
How Cloud Computing Has Intensified Cybersecurity Challenges
Discover the evolving landscape of cybersecurity in this eye-opening article on how rapid cloud adoption creates intensified challenges for businesses. Uncover the hidden risks, understand the impact on data protection and learn strategies to safeguard your organization. Knowledge is power. Read the article and fortify your defenses.
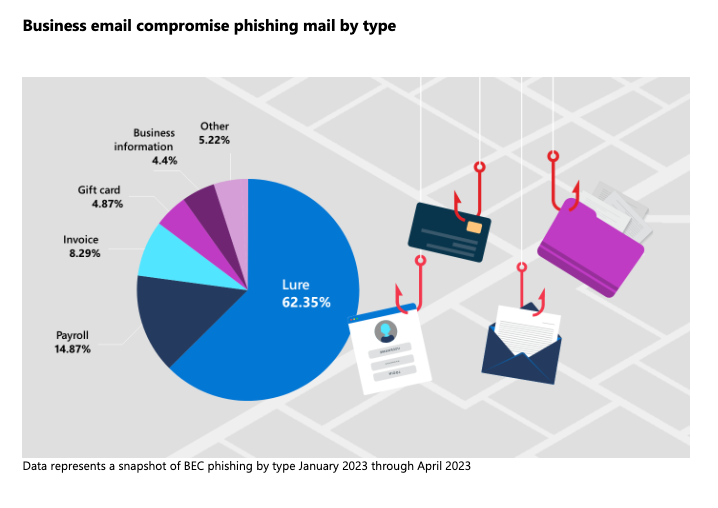
Business email compromise phishing mail by type
Successful BEC (business email compromise) attacks cost organizations hundreds of millions of dollars annually. What are the most common types of BEC attacks? View this infographic for an at-a-glance.
Hybrid Work is Here to Stay
Hybrid work is not simply a way to maintain work-life balance or cope with a crisis. It’s a powerful tool that can help to reimagine entire organizations—for greater efficiency, engagement and innovation. Through a strategic partnership, Microsoft and VMware can help your organization transform hybrid work into a high-value asset by enabling a productive anywhere workspace. The eBook, “Hybrid Work is Here to Stay,” explores how Microsoft and VMware can help you create a hybrid workplace that accelerates innovation with the right technology, culture and leadership. Download your complimentary copy of the eBook now. Contact us to learn how Mowry International can help you develop the vision, strategy and flexible IT infrastructure needed to adapt to new, more flexible ways of working.
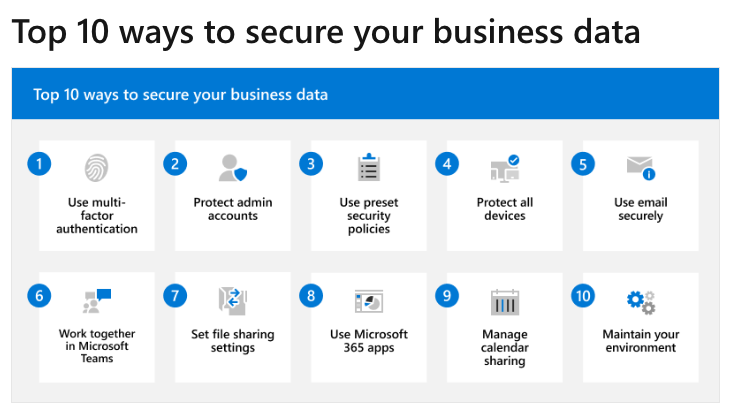
Top 10 Ways to Secure Your Business Data
Microsoft 365 Business Basic, Standard, and Premium include anti-phishing, antispam and antimalware protection. Microsoft 365 Business Premium includes even more security capabilities, such as advanced threat protection for devices (also referred to as endpoints), email and collaboration, and information protection. This article and table summarize recommendations for securing your business data with various Microsoft 365 subscriptions.
Lufthansa Cargo
Microsoft Dynamics 365 helps Lufthansa Cargo manage its complex logistics operations with a unified platform for customer relationship management (CRM), order management and financial reporting. With Dynamics 365, Lufthansa Cargo has been able to streamline processes, reduce manual work and improve customer satisfaction. Get the story on how Lufthansa Cargo benefits from a Dynamics 354 platform that delivers real-time insights on shipment status and financial performance to enable data-driven decisions while boosting operational efficiency.
Shifting tactics fuel surge in business email compromise
In this eye-opening Microsoft Security Insider article, explore the shifting tactics employed by cybercriminals in business email compromise attacks. Read “Shifting tactics fuel surge in business email compromise” to gain valuable insights into cybercriminals’ strategies, techniques and motivations. Discover three steps you need to take to fortify defenses and mitigate potential risks. Knowledge is power. Build yours with this 9-minute read. Start now.
Virtual Desktops on Microsoft Azure
Citrix Virtual Desktops service simplifies Windows deployment. You can deploy desktops quickly, manage at scale and deliver a rich user access experience from a single management plane. Read this super-short blog for a quick-hitting list of what you can do with Virtual Desktops on Microsoft Azure and how you can get started.